Distributed Denial of Service (DDoS) is a significant cyber security threat to online businesses and digital platforms. These attacks overwhelm a target’s resources, making it inaccessible to legitimate users. As technology evolves, so do attackers’ methodologies, leading to various DDoS types. Understanding these can help organisations prepare and protect their digital assets effectively. So, this guide describes the types of cyber security threats.
The Nature and Methodology of DDoS Attacks
DDoS are executed by leveraging multiple compromised computer systems as sources of attack traffic. Computers and IoT devices are infected with malware, turning them into bots (or zombies) that execute an attack on a targeted system. The strength of these attacks lies in their ability to use the combined bandwidth of thousands of devices, making it difficult for the target to distinguish legitimate traffic from malicious traffic.
- Volume-Based Attacks: The Quantitative Approach
Among the most common are volume-based threats, which aim to consume the bandwidth of the victim’s network. These attempts flood the target with a colossal amount of data, overwhelming the network’s ability to process and respond to legitimate requests. The impact is immediate and disruptive, causing slow service for some users and complete service denial for others.
- Protocol Attacks: Targeting the Weak Links
It targets the very fabric of internet communication protocols. Attackers can disrupt the normal communication process by exploiting vulnerabilities in the Layer 3 and 4 protocol stacks. This category includes SYN floods, Ping of Death, and Smurf DDoS, each designed to create significant disruption by exploiting weaknesses in the network layers.
- Application Layer Attacks: The Silent Threat
Far more sinister and difficult to detect are application layer threats. These cyber assaults can fly under the radar by mimicking human behaviour, making them particularly dangerous. They aim to exhaust the resources of a web server, application server, or database server, leading to a denial of service without the massive amounts of traffic characteristic of other DDoS.
- Amplification Attacks: The Force Multiplier
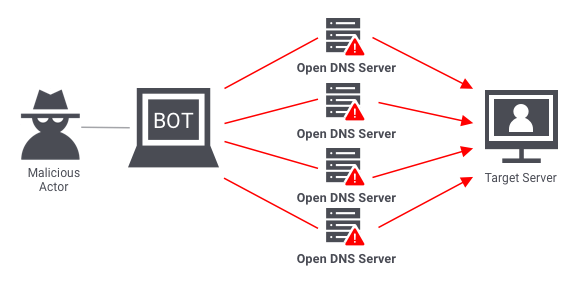
An insidious subset of volume-based attacks, amplification magnifies an attack’s volume by exploiting the functionality of public network services. These attempts leverage the disparity in request and response size: a small query sent to a server triggers a much larger response towards the target. Protocols such as DNS, NTP, and SNMP are commonly exploited. The attacker spoofs the IP address, causing the server to flood the victim with significant responses.
- Reflection Attacks: Misdirection and Mayhem
Closely related to amplification are reflection attacks, which also involve the misuse of legitimate servers. However, their unique aspect is their method of concealing the attacker’s identity. By reflecting the attack traffic off third-party servers before directing it to the victim, attackers can obscure their origin. This not only amplifies the attack but also complicates the process of tracing it back to its source. The combination of reflection and amplification tactics results in powerful assaults that can overwhelm victims with unexpected traffic volumes, complicating defence and mitigation efforts.
The Implications and Impact of DDoS Attacks
The consequences of DDoS attacks extend far beyond temporary inaccessibility or slow network performance. For businesses, the ramifications can be severe, including loss of revenue, erosion of customer trust, and long-term damage to a brand’s reputation. Moreover, the complexity and sophistication of these attacks can stretch the resources of even the most well-prepared organisations.
The threat of DDoS looms over large businesses and digital platforms in the digital age. Understanding the various DDoS types and their potential impact is the first step in developing an effective defence strategy. Staying informed and prepared cannot be overstated as attackers refine their methods. By doing so, organisations can protect their digital assets and ensure operations continuity, safeguarding their reputation and bottom line.